Zoom Phone has emerged as a powerful solution that not only revolutionizes virtual meetings but also enhances traditional phone systems. Zoom Phone offers the potential to streamline communication, improve collaboration and elevate productivity for businesses of all sizes. Whether you are an entrepreneur, a team leader or a remote worker, understanding the transformative potential of Zoom Phone – while being mindful of the related security considerations – can help you stay connected and succeed in this rapidly evolving digital landscape.
What Are Zoom Phone’s Capabilities?
Zoom Phone is a cloud-based enterprise phone system that offers various features, such as video conferencing, voice calling, messaging and file sharing. One of the benefits of using Zoom Phone is its scalability. It is a cloud-based service, which means small or large businesses can easily add or remove phone lines as needed.
In the wake of the global pandemic, the way we communicate and collaborate has undergone a profound transformation. With remote work becoming the new norm in many industries, organizations worldwide have had to rapidly adapt to virtual environments, seeking effective tools to connect their teams and maintain seamless communication. Zoom Phone is a game-changer, addressing the escalating demand for reliable and feature-rich communication systems. By seamlessly integrating voice calls, video conferencing, and messaging, Zoom Phone offers a comprehensive solution that not only caters to the evolving needs of businesses but also ensures the uninterrupted flow of communication in these challenging times.
Additionally, Zoom Phone is designed with security in mind, using encryption to protect communication and data. Utilizing standards-based Voice-over-Internet-Protocol (VoIP) to deliver best-in-class voice services, Zoom Phone provides a secure and reliable alternative to traditional on-premise PBX solutions. Session Initiation Protocol (SIP) shows call setup and in-call features.
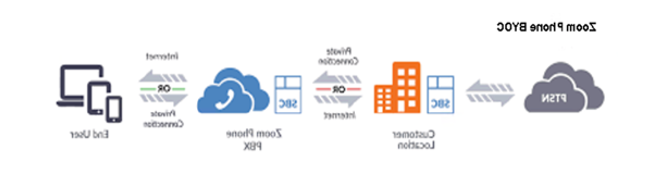
Threat Modeling Proactively
Threat modeling systematically identifies and prioritizes potential threats and vulnerabilities in a system or application. It is a proactive process that involves analyzing the system or application from an attacker’s perspective to identify potential vulnerabilities that do exploit.

Threat modeling identifies and prioritizes potential risks based on their likelihood and impact. By understanding potential threats and vulnerabilities, organizations can develop strategies and implement controls to mitigate those risks and protect their assets.
1. A Novel Methodology for Proactive Threat Assessment and Mitigation
1.1 Conducting a Proactive Analysis Through Threat Modeling for Enhanced Security
Potential Attackers and Their Motivations:
- Cybercriminals who are interested in stealing sensitive information, such as usernames, passwords or credit card information
- Nation-state actors who may be interested in conducting espionage or disrupting communications
- Malicious insiders who may have access to sensitive information and seek to exploit it for personal gain or to harm the organization
- Hacktivists who may seek to disrupt communications to promote a particular agenda
The attack surface of Zoom Phone includes the following components:
- The Zoom Phone client software and user interfaces
- The back-end infrastructure that supports the system
- The network connections used by the system, including internet connectivity and internal network connections
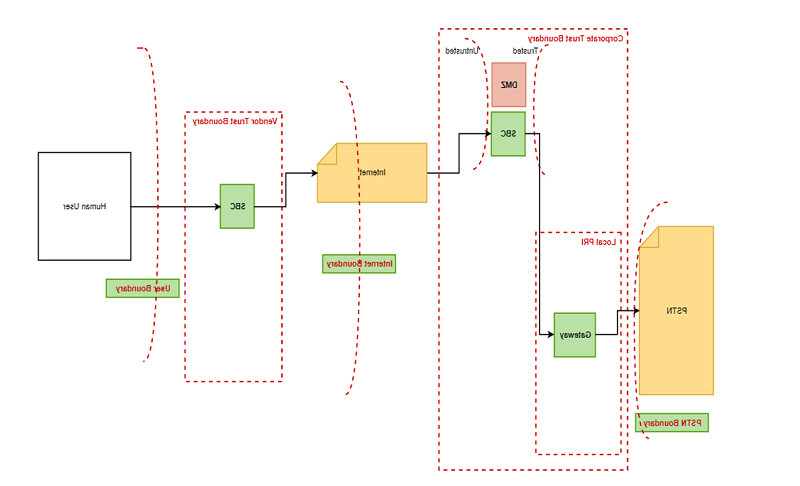
The following are potential vulnerabilities in Zoom Phone:
- The Zoom Phone client software may be vulnerable to exploitation via software vulnerabilities, such as buffer overflow or SQL injection attacks.
- The back-end infrastructure that supports the system may be vulnerable to DDoS attacks or other attacks that could disrupt the system.
- The system’s network connections may be susceptible to interception, eavesdropping or man-in-the-middle attacks.
The threat modeling analysis of Zoom Phone does perform using the STRIDE:
STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) framework is widely used for threat modeling analysis and helps identify potential threats and their associated risks. The study examines the various components of Zoom Phone, including its network infrastructure, software components and communication protocols.
- Spoofing: The Zoom Phone system can be vulnerable to spoofing attacks. An attacker can impersonate a legitimate user or device and gain unauthorized access to the system. It can result in the compromise of sensitive information and data.
- Tampering: The Zoom Phone system can be vulnerable to tampering attacks, where an attacker can modify the system's data or settings, leading to unauthorized access or disruption of services.
- Repudiation: The Zoom Phone system can be vulnerable to repudiation attacks, where attackers can deny their involvement in a particular activity or transaction, leading to difficulties in identifying the responsible party.
- Information Disclosure: The Zoom Phone system can be vulnerable to information disclosure attacks, where an attacker can gain unauthorized access to sensitive information and data, leading to privacy breaches.
- Denial of Service: The Zoom Phone system can be vulnerable to denial of service attacks, where an attacker can disrupt the availability of services by overwhelming the system with traffic or other means.
- Elevation of Privilege: The Zoom Phone system can be vulnerable to a peak of privilege attacks, where an attacker can gain unauthorized access to privileged resources, compromising the system’s security.
The following are potential threats to Zoom Phone and their likelihood and impact:
- Cybercriminals could exploit a Zoom Phone client software vulnerability to intercept or manipulate calls or access sensitive information. Likelihood: Medium; Impact: High.
- A DDoS attack could disrupt communications and prevent users from accessing the system. Likelihood: Medium; Impact: High.
- A malicious insider could access sensitive information and exploit it for personal gain or to harm the organization. Likelihood: Low; Impact: High.
- A hacktivist could disrupt communications to promote a particular agenda. Likelihood: Low; Impact: Medium.
Mitigate the risks identified in the threat modeling exercise:
- Implement authentication and authorization mechanisms to prevent spoofing attacks.
- Use encryption and digital signatures to prevent tampering attacks.
- Implement logging and auditing mechanisms to detect and prevent repudiation attacks.
- Use encryption and access controls to prevent information disclosure attacks.
- Implement load balancing and redundancy mechanisms to prevent denial of service attacks.
- Use role-based access control mechanisms to prevent the elevation of privilege attacks.
1.2 How Threat Modeling Empowers Audit, Governance, Privacy, Risk and Security Professionals
- Threat modeling helps audit professionals develop plans that focus on areas of high risk and prioritize their efforts accordingly.
- Threat modeling helps governance professionals develop policies and procedures that address the identified risks and ensure the organization is adequately protected.
- Threat modeling helps privacy professionals develop privacy policies and procedures that address the identified risks and ensure that the organization complies with relevant privacy laws and regulations.
- Threat modeling helps risk professionals develop risk management plans that prioritize areas of high risk and allocate resources accordingly.
- Threat modeling helps security professionals develop security plans that address the identified risks and ensure the system or application is secure.
An Increasing Need for Secure Communications
In today’s increasingly connected world, the need for secure communication platforms is more critical than ever before. The threat modeling exercise conducted for Zoom Phone has highlighted potential risks and vulnerabilities that should be addressed to ensure the security of user data and the system itself. By implementing the risk mitigation strategies suggested, we can proactively protect Zoom Phone communications and build trust with our users. With a continuous commitment to security and privacy, Zoom Phone can continue to provide its users with a reliable and secure platform for their communication needs.
